Audit Trails allow our Customers to have full visibility into both human and system actions regarding their Organization.
The Audit Trails you see are "hot" stored in the Database for fast indexing and retained for 90 days.
The same records are also forwarded to an immutable storage for and retained for a full year.
In case of dispute, for a valid reason or under legal request we will give you access to the immutable records.
INFO: Immutable means we can NOT change them in any way after the first write, this is guaranteed by a third party provider.
We offer full, crystal clear access to Audit Trails to every customer because we strongly believe in transparency and accountability.
Understanding Audit Trails
Each record is meant to show WHO did WHAT WHERE and WHEN
- Timestamp shows exactly when the record was created - WHEN
- Description is a brief summary of what happened - WHAT
- Actor is the entity, human name or SYSTEM, who performed the action - WHO
- Event Type is defines the type of event - WHERE
- Event Category is a more general categorization of the event
INFO: By clicking the down arrow the record is expanded and further details can be seen.
Actor, Event Type and Category of each event can be clicked to filter records pertaining a specific category, or performed by an actor.
By clicking the link icons a trail of records related to a specific Resource ID ("entity") can be seen.
This allows to see everything that happen to a specific resource, like the lifecycle of an Event
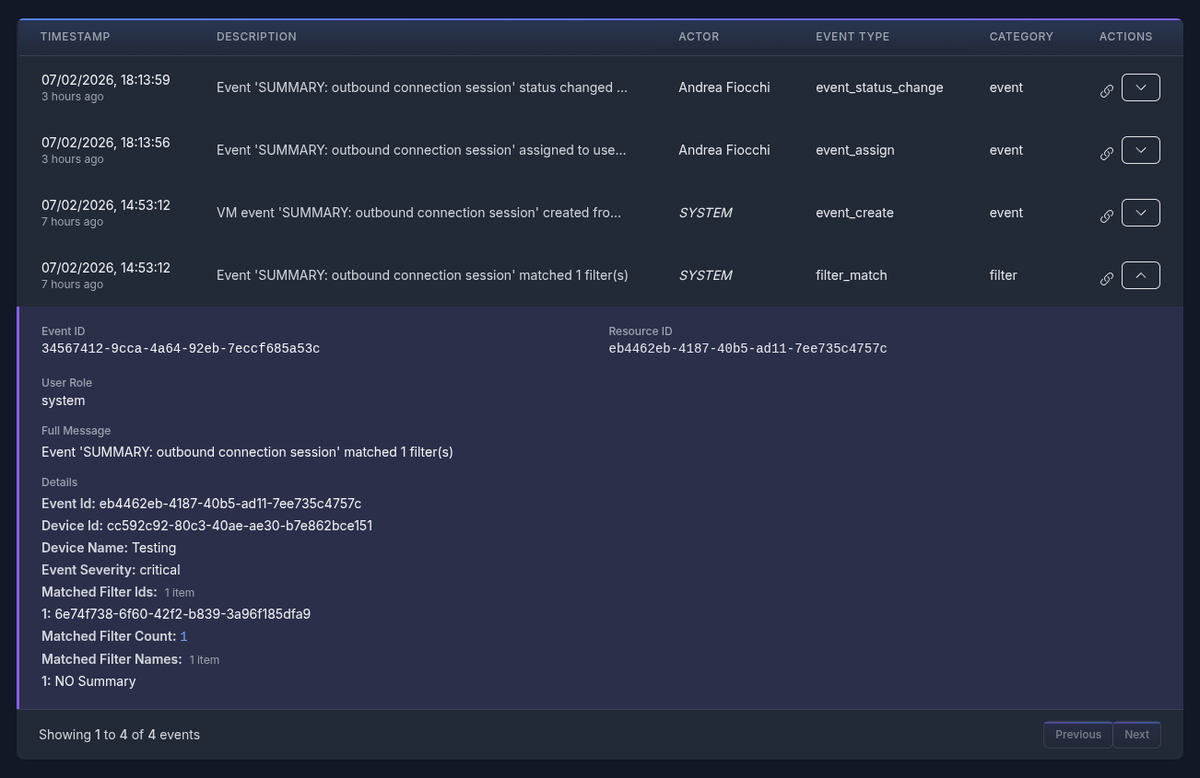
From the example above, we can see exactly what happened to the "SUMMARY: outbound connection session" security event.
- Initially it was matched by the "NO Summary" Filter. This is an automated SYSTEM action.
- The event was then created and added to the platform. Another SYSTEM action.
- Later the administrator Andrea Fiocchi assigned himself the event and its status became in_progress
- Finally, Andrea Fiocchi marked the event as resolved.